
Cisco Industrial Threat Defense
Protect industrial operations against cyberthreats by gaining visibility and control over your OT and ICS
Cisco Industrial Security for your IoT, OT, and ICS
Gain visibility over your Operational Technology (OT) and build comprehensive IoT security capabilities with Cisco Industrial Threat Defense.

Note: For our full product catalog, please visit our Cisco Security focused site at SecureCloudGuard.com.
Why Cisco Industrial Threat Defense?
From OT visibility to zero-trust and all the way to a converged IT/OT security strategy, rely on Cisco through
your industrial security journey.
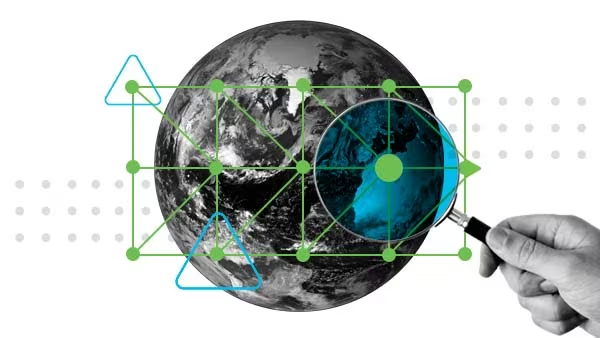
OT visibility and threat detection
Assess your risks. Identify what's connected. Industrial Threat Defense leverages your existing network to give you comprehensive visibility, so you can detect threats at scale and strengthen your industrial security posture.

Industrial network segmentation
Prevent threats from spreading. Whether you're building your industrial DMZ, creating zones and conduits, or migrating to a zero-trust micro-segmentation strategy, Industrial Threat Defense has you covered.
Converged threat investigation and remediation
Leverage your existing security tools and practices. Industrial Threat Defense adds OT security events and context to your security operations center (SOC), so that you can build a truly converged IT/OT security strategy.
Cisco Industrial Threat Defense Video
Cisco Industrial Threat Defense is your one-stop industrial cybersecurity solution. Extend IT security to IoT/OT and accelerate your digital transformation.
Cisco Industrial Threat Defense for…
Manufacturing
Facilitate digital transformation by enforcing zones and conduits to secure production cells.
Oil and gas operators
Help ensure operations safety, uptime, and compliance with a holistic approach to securing assets in harsh environments.
Power utilities
Secure substations by gaining visibility and control over distributed grid assets.
Water utilities
Develop IoT readiness and system efficiencies by securing wastewater and water-distribution plants.
Port and terminal operators
Help prevent revenue losses and improve automation by protecting terminal assets against cyberthreats.
Transportation
Improve overall safety, efficiency, and comfort for travelers through a secure network infrastructure.
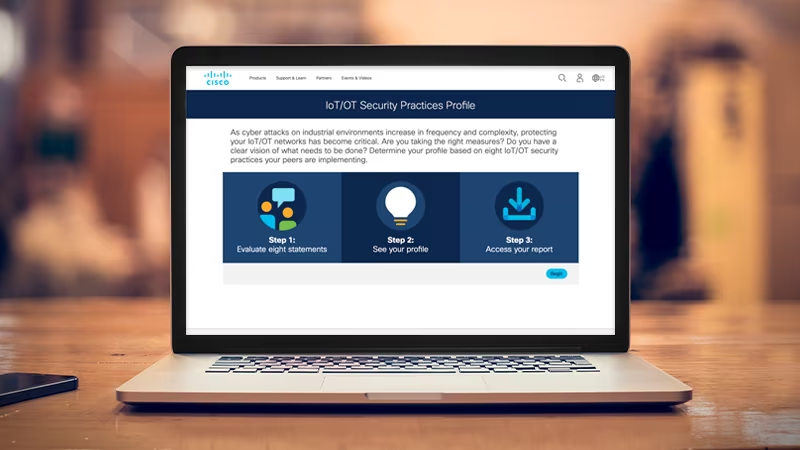
How mature is your IoT security practice?
Are you taking the right measures to protect your industrial operations? Determine your profile based on security practices that other industrial organizations are implementing.
Build your industrial IoT security foundations
Gain OT visibility to drive security improvements
Assess your OT security posture. Inventory industrial assets. Identify vulnerabilities. Detect process anomalies. Leverage these insights to improve operational efficiency and build ideal security policies.
Reduce the attack surface by protecting cells, zones, or substations
Enforce zone segmentation. Detect malware and intrusions. Protect assets you can't patch. Block unwanted industrial control system (ICS) commands. Stop network threats with our rugged industrial firewalls.
Investigate and remediate threats across IT and OT
Give your IT SOC visibility into your OT network. Enrich OT security events with threat intelligence from your other security tools. Build playbooks to orchestrate remediation without disrupting OT processes.
Implement zero-trust security in your industrial settings
Enforce micro-segmentation policies
Extend software-based network segmentation policies to your industrial control network. Policies are applied dynamically based on zones and conduits defined by OT teams.
Protect industrial workstations from malware
Reduce the attack surface by using advanced endpoint detection and response (EDR) powered by Cisco Talos. Find sophisticated attacks faster and accelerate remediation to maintain uptime.
Secure remote access to industrial networks and devices
Empower OT teams to perform critical day-to-day operations on remote or distributed industrial equipment easily and securely.
Use zero-trust authentication for users and devices
Verify user identity and device security for access to industrial networks, using Cisco Secure Access by Duo adaptive multi-factor authentication.

Threat intelligence and OT security services you can count on
Leading intelligence for comprehensive protection
Industrial Threat Defense harnesses the power of Cisco Talos, our industry-leading threat-intelligence group and the official developer of Snort signatures.
Get help from OT security experts
When you need to assess your OT security to define your plans or get help to implement your OT security tools, reach out to Cisco's Customer Experience teams.
Get incident-response support
Cisco Talos provides a full suite of proactive and emergency services to help you prepare, test your defense, respond, and recover from a breach.

